Table of Contents
- Introduction
- Overview
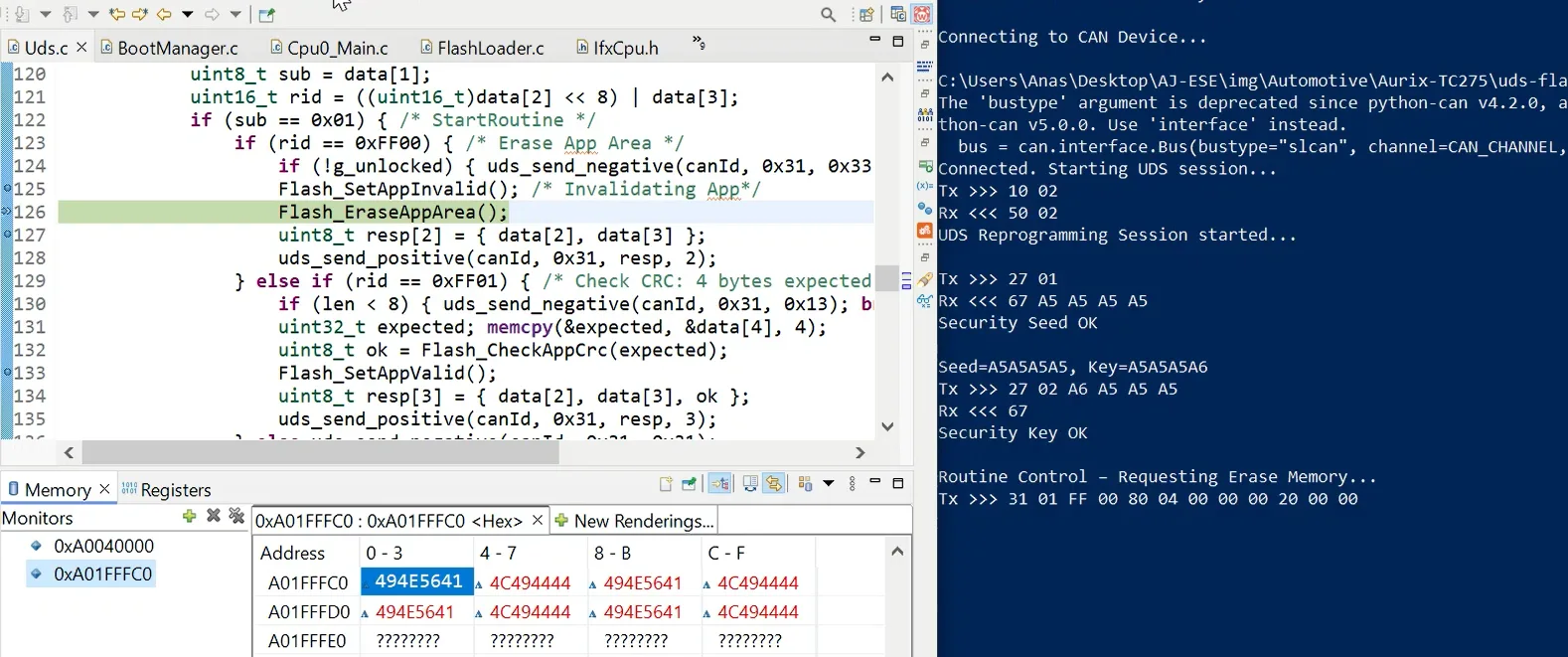
- Signature check process
- Bootloader and HSM communication
- Implementation example
Access Restricted
This article is only available to business partners. If you already have the password, please enter it below. Otherwise, please request access.